F5 Porter's Five Forces Analysis
Fully Editable
Tailor To Your Needs In Excel Or Sheets
Professional Design
Trusted, Industry-Standard Templates
Pre-Built
For Quick And Efficient Use
No Expertise Is Needed
Easy To Follow
F5 Bundle
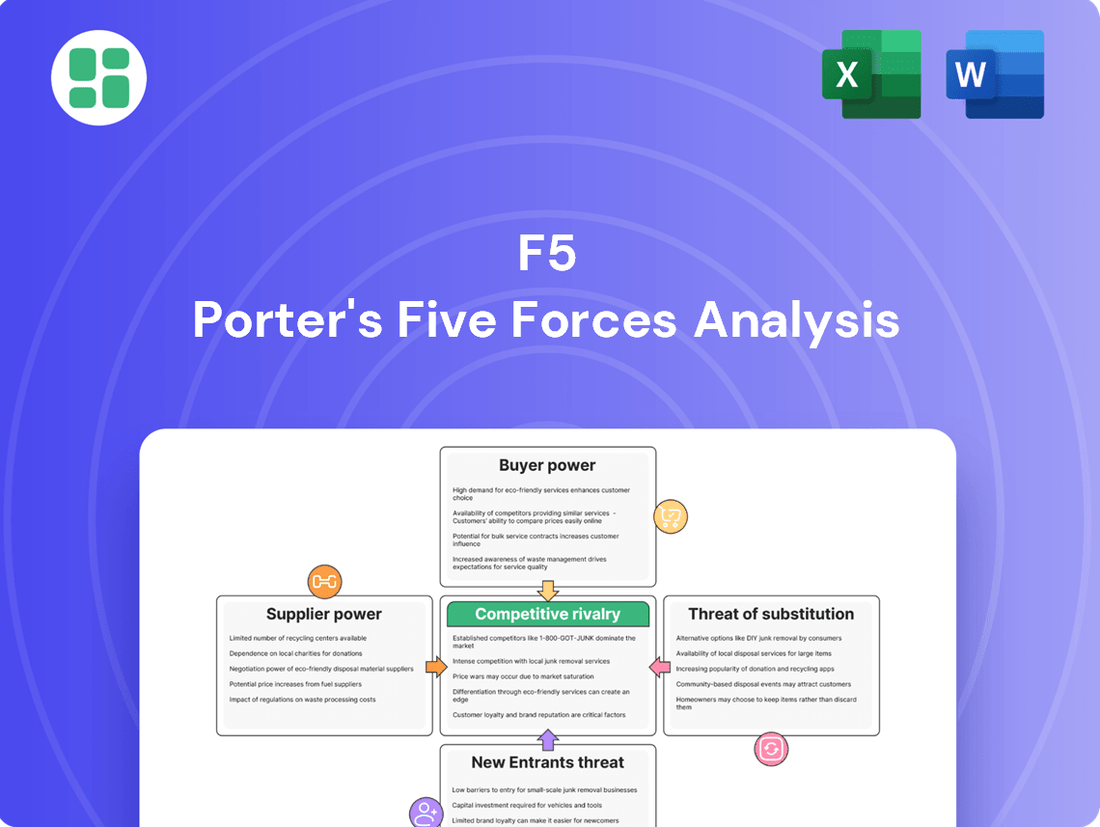
Porter's Five Forces Analysis reveals the competitive landscape F5 navigates, detailing the power of buyers, suppliers, and the threat of new entrants and substitutes. Understanding these forces is crucial for F5's strategic positioning and long-term success. Ready to move beyond the basics? Get a full strategic breakdown of F5’s market position, competitive intensity, and external threats—all in one powerful analysis.
Suppliers Bargaining Power
F5's reliance on specialized hardware components for its BIG-IP iSeries and rSeries platforms means certain semiconductor suppliers hold significant bargaining power. The unique nature of high-performance networking chips can limit the number of viable suppliers, potentially leading to increased costs and longer lead times for F5. For instance, in 2024, the global semiconductor shortage continued to impact lead times for certain advanced components, underscoring this vulnerability.
As F5 increasingly relies on software and cloud infrastructure, the bargaining power of these suppliers grows. This shift from hardware to software means F5's operational success is more tied to the availability and terms offered by cloud giants like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). For instance, in 2023, AWS held approximately 31% of the cloud infrastructure market, demonstrating its significant influence.
The need for deep integration with these cloud platforms for F5's security and application delivery solutions creates a degree of dependency. While these providers offer a wide array of services, the specialized integration required for F5's offerings could lead to considerable switching costs if F5 were to change its primary cloud partners, thereby enhancing supplier leverage.
The demand for highly skilled professionals in cybersecurity, application delivery, cloud architecture, and AI/machine learning significantly bolsters supplier power. F5 must actively recruit and retain top talent to drive innovation and maintain its competitive advantage in a fast-paced tech environment. The limited availability of these specialized skills can lead to increased labor expenses and impact project schedules.
Open-Source Software Dependencies and Associated Risks
F5, like many tech companies, relies heavily on open-source software (OSS). This reliance, while beneficial for cost and speed, exposes F5 to risks such as unpatched vulnerabilities and compromised dependencies. For instance, a 2023 report by Snyk found that 80% of all codebases contained open-source components with known security issues.
The stability and security of F5's products are thus indirectly tied to the practices of the open-source community. Managing these dependencies effectively is crucial, involving rigorous internal processes and tools to identify and address potential threats. This includes continuous monitoring for new vulnerabilities in the OSS components they utilize.
- OSS Integration Risks: F5's use of open-source software, while cost-effective, introduces risks from known vulnerabilities and unmaintained code.
- Supply Chain Attacks: A significant concern is the potential for supply chain attacks where legitimate OSS packages are compromised, impacting F5's software.
- Dependency Management: Robust internal processes and tools are essential for F5 to manage security and maintenance risks associated with its OSS dependencies.
- Community Reliance: F5's operational integrity is influenced by the security practices and stability of the broader open-source community.
Standardization vs. Customization of Inputs
The degree to which F5 can source standardized components versus requiring highly customized inputs significantly impacts supplier power. When F5 utilizes more commoditized hardware or standard software libraries, supplier power tends to be lower because there's a greater number of competing suppliers. This allows F5 to negotiate more favorable terms.
Conversely, for specialized application delivery controllers (ADCs) or Web Application Firewalls (WAFs) that demand unique intellectual property or highly integrated chipsets, suppliers possessing these specific capabilities wield greater bargaining power. For instance, a supplier of a proprietary ASIC crucial for F5's next-generation hardware could command higher prices.
- Standardized Inputs: Lower supplier power due to broader supplier base and increased competition.
- Customized Inputs: Higher supplier power, especially for unique IP or integrated components.
- F5's Strategy: Long-standing relationships with key suppliers are vital for managing this power dynamic in high-performance systems.
The bargaining power of suppliers for F5 Networks is influenced by the concentration of suppliers for critical components and the uniqueness of the inputs required. When F5 needs highly specialized hardware, like advanced semiconductors for its BIG-IP platforms, suppliers with limited competition can dictate terms, potentially increasing costs.
| Supplier Type | Impact on F5 | Example (2024/2025 Context) |
|---|---|---|
| Semiconductor Manufacturers | High bargaining power due to specialization and limited competition for advanced chips. | Continued lead time challenges for high-performance networking silicon, impacting production schedules. |
| Cloud Infrastructure Providers | Growing power as F5 increases reliance on cloud-based solutions. | AWS, Azure, GCP hold significant market share, influencing service terms and integration requirements. |
| Open-Source Software Maintainers | Indirect power through dependency risks and security vulnerabilities. | High prevalence of OSS with known security issues (e.g., Snyk reports) necessitates robust internal management. |
What is included in the product
This analysis unpacks the competitive intensity within F5's market by examining the power of buyers and suppliers, the threat of new entrants and substitutes, and the rivalry among existing competitors.
Quickly identify and mitigate competitive threats by visualizing the intensity of all five forces, enabling proactive strategy adjustments.
Customers Bargaining Power
F5's core offerings, like Application Delivery Controllers (ADCs) and Web Application Firewalls (WAFs), are deeply integrated into a company's essential IT systems. These solutions manage and safeguard application traffic, making them foundational components. For instance, in 2023, F5 reported that its security solutions played a role in protecting billions of application requests daily for its enterprise clients.
The intricate nature of replacing these critical systems presents substantial switching costs for customers. This involves complex processes such as reconfiguring extensive network setups, retraining IT personnel on new platforms, and ensuring uninterrupted security protocols. Such operational hurdles make it challenging for businesses to migrate to competing vendors, thereby strengthening F5's leverage with its customer base.
The criticality of application performance and security significantly curtails customer bargaining power. F5's solutions are fundamental to ensuring that a customer's applications and APIs remain available, performant, and secure, which are now the backbone of most businesses.
Given that application downtime or security breaches can result in substantial financial losses, severe reputational damage, and costly regulatory penalties, customers place a premium on F5's reliability and robust security features. This high level of dependence means that customers are less likely to push for significant price reductions, as the cost of failure far outweighs minor savings.
In 2024, the increasing reliance on digital services means that the impact of poor application performance or security is amplified. For instance, a major data breach in 2024 could cost a company millions in fines and lost trust. F5's positioning as a guardian of every application and API reinforces its indispensable role, thereby diminishing the bargaining leverage of its customers.
F5 Networks serves a broad spectrum of clients, from massive enterprises and critical service providers to government agencies and popular consumer brands. This extensive reach spans vital sectors such as banking, financial services, and insurance (BFSI), retail, information technology and telecommunications, and healthcare.
This wide distribution of customers significantly diminishes the bargaining power of any single client or a small cluster of clients. F5's business model thrives on not being overly dependent on a handful of major accounts, which naturally limits the leverage any one customer can exert.
The company's customer base is also spread across numerous industries. This diversification across different verticals effectively buffers F5 against the risks associated with concentrated demand, ensuring stability even if one sector experiences a downturn.
Access to Alternative Solutions and Cloud-Native Offerings
Customers possess significant bargaining power due to the availability of numerous alternative solutions. Beyond direct competitors like Citrix ADC, Akamai, Cloudflare, Imperva, and Fortinet, open-source options such as NGINX, HAProxy, and ModSecurity offer cost-effective alternatives. This broad competitive landscape allows customers to negotiate pricing and terms more effectively.
The rise of cloud-native architectures and microservices further amplifies customer leverage. Organizations increasingly integrate services directly from hyperscalers like AWS, Azure, and Google Cloud, potentially reducing their reliance on specialized vendors like F5. For instance, AWS's Elastic Load Balancing or Azure Application Gateway can fulfill many application delivery needs, putting downward pressure on F5's pricing and feature differentiation.
- Competitor Landscape: F5 faces direct competition from established players like Citrix and emerging cloud-focused security providers.
- Open-Source Alternatives: Widely adopted open-source solutions provide viable, lower-cost options for many application delivery and security functions.
- Cloud Provider Services: Hyperscalers offer integrated, often more cost-effective, application delivery and security features within their cloud platforms.
- Customer Choice: The proliferation of alternatives empowers customers to demand better pricing and more flexible feature sets from F5.
Customer Sophistication and Customization Needs
F5's customer base is largely comprised of large, technologically advanced enterprises. These organizations typically operate complex application environments and have very specific needs regarding security and application delivery. Their sophistication means they are well-informed buyers.
These sophisticated clients often demand tailored solutions, extensive professional services, and seamless integration with their existing IT infrastructure. This can translate into significant bargaining power for them.
While F5 is known for its customization and service offerings, highly particular demands from these powerful customers can compel F5 to continually invest in research and development and bolster its support infrastructure. For instance, in 2024, F5 reported a significant portion of its revenue derived from services and support contracts, underscoring the importance of meeting these customer needs.
- Customer Sophistication: F5's clients are typically large enterprises with deep technical expertise.
- Customization Demands: Customers often require bespoke solutions to meet unique application and security needs.
- Service & Integration Focus: Strong emphasis is placed on professional services and integration capabilities.
- Impact on F5: High customer demands necessitate ongoing R&D investment and robust support.
Customers possess considerable bargaining power due to the wide array of alternative solutions available. This includes direct competitors, open-source options, and integrated services from cloud hyperscalers. For example, in 2024, the market for application delivery controllers and web application firewalls is highly competitive, with many vendors offering comparable functionalities, thereby increasing customer leverage.
The increasing adoption of cloud-native architectures and microservices by businesses further empowers customers. They can leverage services from providers like AWS, Azure, and Google Cloud, potentially reducing their dependence on specialized vendors like F5 and exerting downward pressure on pricing.
F5's diverse customer base, spread across various industries and geographies, limits the bargaining power of any single client. However, the sophistication of its enterprise clients, who often demand tailored solutions and extensive support, can translate into significant leverage, compelling F5 to invest continuously in R&D and service enhancements.
| Factor | Impact on F5 | Data/Example (2024) |
|---|---|---|
| Availability of Alternatives | Increases customer bargaining power | Highly competitive market with numerous vendors and open-source options. |
| Cloud Provider Services | Reduces customer reliance on F5, increasing leverage | Hyperscalers offer integrated ADC/WAF functionalities, pressuring F5 pricing. |
| Customer Sophistication | Can increase bargaining power through demand for customization | Large enterprises require tailored solutions, driving F5's R&D and service investments. |
| Customer Concentration | Low concentration limits individual customer leverage | F5 serves a broad base, reducing dependence on any single account. |
Full Version Awaits
F5 Porter's Five Forces Analysis
This preview showcases the complete F5 Porter's Five Forces Analysis, providing a thorough examination of competitive forces within an industry. The document you see here is precisely what you will receive immediately after purchase, ensuring no surprises and full readiness for your strategic planning needs.
Rivalry Among Competitors
The application delivery and security market is a battleground, with F5 facing fierce competition from established rivals like Citrix, Akamai, Imperva, Fortinet, and Radware. These companies have long-standing market presence and robust product portfolios.
Adding to the pressure are the major cloud providers – AWS, Microsoft Azure, and Google Cloud. They are increasingly offering their own native Application Delivery Controller (ADC), Web Application Firewall (WAF), and API security services, often bundled with their cloud infrastructure. This makes it challenging for dedicated providers like F5 to compete on price and integration within cloud environments.
For instance, in 2024, cloud providers continued to expand their security and networking services, directly encroaching on traditional ADC and WAF markets. Organizations are increasingly looking for integrated solutions, making the cloud giants attractive alternatives.
This intense rivalry necessitates constant innovation from F5. The company must continually enhance its offerings and find ways to differentiate itself, whether through advanced features, specialized solutions, or superior customer support, to maintain its market position in this dynamic landscape.
The competitive landscape for F5 is defined by a relentless pace of technological change, with cloud-native architectures, AI-powered security, and edge computing at the forefront. This necessitates continuous innovation as rivals frequently launch new features and deployment options, ranging from traditional on-premises solutions to flexible cloud and hybrid models.
To maintain its edge, F5 must aggressively pursue advancements, especially in software and AI. The company's 2025 technology roadmap specifically identifies WebAssembly and AI as critical areas for future growth and competitive advantage, underscoring the industry's demand for cutting-edge solutions.
The competitive landscape is intensifying as the industry pivots from selling physical hardware to offering software-defined solutions and subscription services. This shift means companies are now vying for dominance based on the agility and features of their software, alongside the predictable income from recurring revenue streams, rather than solely on the raw performance of their hardware appliances.
F5 Networks is actively navigating this transformation, aiming to solidify its position as a leader in software and security. This strategic move is crucial for staying competitive in a market that increasingly values flexibility and ongoing service delivery. For instance, F5's commitment to this transition is evident in its financial performance, with recurring revenue accounting for a significant 73% of its total revenue in Q3 FY25, underscoring the success of its software and subscription-focused strategy.
High Fixed Costs and R&D Investment Requirements
Developing and maintaining advanced application delivery and security solutions demands substantial investment in research and development, alongside sales and support infrastructure. This inherently leads to high fixed costs for companies like F5 Networks.
To achieve profitability, these companies must attain significant economies of scale and cultivate a broad customer base. For instance, F5 Networks reported that in fiscal year 2023, their operating expenses were $2.3 billion, highlighting the substantial fixed costs associated with their business model.
The continuous need for innovation, particularly in areas such as AI-driven threat detection and safeguarding AI workloads against data leakage, further escalates these expenditures. This ongoing R&D commitment is crucial for staying competitive in the rapidly evolving cybersecurity landscape.
- High R&D Investment: Companies in this sector must consistently invest in developing new technologies to address emerging threats and customer needs.
- Significant Sales & Support Infrastructure: Building and maintaining a global sales force and customer support network represents a major fixed cost.
- Economies of Scale Necessity: Larger market share allows companies to spread these high fixed costs over more units, improving profitability.
- Increasing AI Security Costs: The growing importance of AI means companies must invest in specialized security solutions, adding to R&D and operational expenses.
Market Growth and Opportunities in Emerging Areas
Despite the competitive landscape, F5 operates in markets with robust growth. The Application Delivery Controllers (ADC), Web Application Firewalls (WAF), and API Security sectors are all expanding significantly. This expansion is fueled by the escalating threat of cyberattacks, the ongoing digital transformation initiatives across industries, widespread cloud adoption, and the increasing use of APIs.
This dynamic market environment presents substantial opportunities for F5. The company is particularly well-positioned to capitalize on high-growth segments. For instance, the API security market is projected to grow at a compound annual growth rate (CAGR) of 32.8% between 2024 and 2025. Furthermore, F5's focus on cloud-native solutions aligns with the broader industry trend towards cloud adoption.
- Market Growth Drivers: Increasing cyber threats, digital transformation, cloud adoption, and API proliferation are fueling expansion in ADC, WAF, and API Security markets.
- F5's Opportunity: The overall market expansion provides avenues for F5 to grow its business.
- High-Growth Segments: API Security is a key area, expected to see a CAGR of 32.8% from 2024-2025.
- Cloud-Native Focus: F5's investment in cloud-native solutions taps into a significant growth trend.
F5 faces intense competition from established players like Citrix and Akamai, as well as major cloud providers such as AWS, Microsoft Azure, and Google Cloud, who increasingly offer integrated native services. This rivalry is amplified by the rapid pace of technological change, with cloud-native architectures and AI-powered security demanding continuous innovation from F5. The industry's shift towards software-defined solutions and subscription models means companies are competing on feature agility and recurring revenue, a trend F5 is actively embracing, with recurring revenue making up 73% of its total revenue in Q3 FY25.
| Competitor | Key Offerings | Market Position |
|---|---|---|
| Citrix | Application Delivery, Virtualization | Established, strong in enterprise |
| Akamai | CDN, Security, Edge Computing | Leading CDN, expanding security |
| AWS | Cloud Infrastructure, Native ADC/WAF | Dominant cloud provider, integrated services |
| Microsoft Azure | Cloud Infrastructure, Native ADC/WAF | Major cloud provider, growing integrated services |
| Google Cloud | Cloud Infrastructure, Native ADC/WAF | Key cloud provider, expanding integrated services |
SSubstitutes Threaten
A major substitute threat to traditional application delivery and security services comes from the native offerings of hyperscale cloud providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud. These providers offer integrated solutions such as elastic load balancing, web application firewalls (WAFs), and content delivery networks (CDNs) directly within their cloud platforms.
For businesses heavily invested in a single public cloud, these native services can appear more cost-effective and simpler to manage due to their inherent integration. For instance, AWS's Application Load Balancer (ALB) and Azure's Application Gateway provide robust Layer 7 load balancing and security features that compete directly with specialized hardware or software solutions.
The rapid expansion of the cloud-native platforms market, which saw global public cloud services revenue reach an estimated $600 billion in 2024, underscores the growing adoption of these integrated alternatives. This growth presents a significant challenge to established players who may not offer the same level of seamless integration within these dominant cloud ecosystems.
Open-source software presents a significant threat of substitutes for F5's offerings. Solutions like NGINX, which F5 itself acquired, and HAProxy provide robust application delivery capabilities at a fraction of the cost, or even for free. For instance, NGINX is widely adopted, powering a substantial portion of the world's busiest websites, indicating its strong market presence as a substitute.
Furthermore, the rise of do-it-yourself (DIY) approaches, where larger enterprises develop bespoke solutions for application delivery and security, bypasses the need for commercial vendors altogether. This trend is fueled by organizations with specialized requirements and the internal expertise to build and maintain their own systems, diminishing the market share available to established players like F5.
Traditional network firewalls, intrusion prevention systems (IPS), and even routers with basic security features can offer partial substitution for F5's more specialized Web Application Firewall (WAF) and Application Delivery Controller (ADC) functionalities. These general-purpose devices might be considered by organizations with limited budgets or less stringent security needs, presenting a lower-cost alternative for basic network protection.
While these substitutes may not match the advanced application-layer security or sophisticated traffic optimization that F5's products provide, they can still fulfill fundamental security and availability requirements. For instance, a robust firewall can block known malicious traffic, and a router can manage basic load balancing, thereby addressing some of the needs typically met by F5 solutions.
However, the escalating sophistication of cyber threats, including advanced persistent threats (APTs) and zero-day exploits, often compels organizations to seek out dedicated, specialized solutions like those offered by F5. The market for cybersecurity solutions is vast, with many companies offering a range of products, but the specific capabilities for deep application inspection and intelligent traffic management remain a differentiator.
Managed Security Services and CDNs with Security Features
Customers increasingly turn to managed security service providers (MSSPs) and Content Delivery Networks (CDNs) that bundle security features. These alternatives often offer Web Application Firewalls (WAF), Distributed Denial of Service (DDoS) protection, and API security as part of a comprehensive package. For example, Akamai, a major CDN provider, reported significant growth in its security services, which directly compete with F5's core offerings, particularly for web-facing applications.
The appeal lies in consolidating security needs with a single vendor, simplifying management and potentially reducing costs. Cloudflare, another prominent CDN, has also aggressively expanded its security portfolio, including WAF and bot management solutions, directly challenging F5's market share. By outsourcing application security to these providers, organizations can leverage their specialized expertise and infrastructure.
- Managed Security Services: Providers offering integrated WAF, DDoS, and API security can directly substitute F5's specialized security products.
- CDN Security Features: Companies like Akamai and Cloudflare provide robust WAF and DDoS mitigation, often bundled with their core CDN services, presenting a competitive alternative.
- Consolidation of Security Needs: Businesses may prefer a single vendor for application security, simplifying management and potentially lowering costs compared to specialized solutions.
- Outsourcing Application Security: The trend of outsourcing security functions allows organizations to leverage third-party expertise and infrastructure, reducing the need for in-house security solutions like those offered by F5.
Emerging Technologies and Shifting Security Paradigms
Emerging technologies are fundamentally changing how organizations approach application security and delivery, presenting a significant threat of substitutes to traditional solutions like those offered by F5. New security paradigms, such as Zero Trust Network Access (ZTNA) solutions, API gateways with integrated security features, and edge computing platforms, can bypass or reduce the reliance on Application Delivery Controllers (ADCs) and Web Application Firewalls (WAFs) for certain functions. For instance, ZTNA models, which grant access based on identity and context rather than network location, can obviate the need for traditional network perimeter security often managed by ADCs. The market for ZTNA solutions saw substantial growth, with reports indicating a compound annual growth rate (CAGR) of over 25% in the years leading up to 2024, demonstrating a clear shift in organizational priorities.
As organizations increasingly adopt these new architectural approaches, the demand for F5's traditional ADCs or WAFs may diminish for specific use cases where these newer technologies offer comparable or superior functionality. This shift is driven by a desire for more granular control, enhanced security posture, and streamlined operations. For example, by 2024, many enterprises were actively migrating workloads to cloud-native environments, where solutions like Kubernetes ingress controllers with integrated security features are becoming more prevalent, directly competing with ADC functionalities.
F5 is actively adapting to this evolving landscape by expanding its portfolio and strategically focusing on a converged application delivery and security platform. This involves integrating its existing offerings with newer technologies and developing solutions that can operate seamlessly within these emerging paradigms. Their acquisition of Volterra in 2021, for example, bolstered their capabilities in edge computing and distributed application services, positioning them to address the threat of substitutes by offering a more comprehensive and adaptable suite of solutions.
- ZTNA solutions offer granular, identity-based access, reducing reliance on traditional network perimeters.
- API gateways with integrated security provide application-specific protection, potentially replacing some WAF functions.
- Edge computing platforms distribute security and delivery closer to users, altering the need for centralized ADCs.
- The growing adoption of cloud-native architectures favors integrated security within orchestration platforms, challenging standalone ADC/WAF models.
The threat of substitutes for application delivery and security services is significant, driven by integrated cloud offerings, open-source solutions, and DIY approaches. Cloud hyperscalers like AWS, Azure, and Google Cloud provide native services that compete directly, especially for businesses already invested in their ecosystems. The global public cloud services market's revenue, estimated to reach $600 billion in 2024, highlights the widespread adoption of these integrated alternatives.
Open-source software, such as NGINX and HAProxy, offers cost-effective alternatives for application delivery, with NGINX powering a substantial portion of the world's busiest websites. Furthermore, enterprises with specialized needs and internal expertise increasingly opt for do-it-yourself solutions, bypassing commercial vendors entirely.
Managed security service providers (MSSPs) and Content Delivery Networks (CDNs) like Akamai and Cloudflare also present a strong substitute threat by bundling security features such as WAF and DDoS protection. This consolidation appeals to businesses seeking simplified management and potentially lower costs by outsourcing application security to specialized third-party providers.
Emerging technologies like Zero Trust Network Access (ZTNA) and API gateways with integrated security are also reshaping the landscape. The substantial growth in ZTNA solutions, with a CAGR exceeding 25% leading up to 2024, indicates a shift away from traditional perimeter security models that ADCs often support.
| Substitute Category | Key Players/Examples | Impact on Traditional Solutions | Market Trend/Data |
| Cloud-Native Offerings | AWS, Azure, Google Cloud | Integrated load balancing, WAF, CDN reducing need for specialized hardware/software. | Global public cloud services revenue projected to exceed $600 billion in 2024. |
| Open-Source Software | NGINX, HAProxy | Cost-effective application delivery, widely adopted for performance. | NGINX powers a significant percentage of high-traffic websites globally. |
| Managed Security Services & CDNs | Akamai, Cloudflare | Bundled WAF, DDoS, API security; simplifies management. | Akamai and Cloudflare report strong growth in security services. |
| Emerging Technologies | ZTNA, API Gateways, Edge Computing | Bypass or reduce reliance on ADCs/WAFs; offer granular, identity-based access. | ZTNA market CAGR over 25% leading up to 2024. |
Entrants Threaten
Entering the application delivery and security market at F5's level demands significant capital for research and development. Developing advanced solutions like Application Delivery Controllers (ADCs), Web Application Firewalls (WAFs), and API security platforms requires immense investment in creating sophisticated hardware and software capable of managing high traffic and complex threats. For instance, F5's own significant R&D spend, which has historically been a substantial portion of their operating expenses, underscores the costly nature of innovation in this space.
Established brand reputation and customer loyalty act as a significant barrier to new entrants. F5 has cultivated a long-standing reputation and deep relationships with large enterprise customers over many years, consistently delivering reliable and high-performance solutions. This history makes it difficult for newcomers to gain the trust of these organizations and displace established vendors.
The critical nature of F5's solutions means customers are often hesitant to switch from a proven provider, fostering strong brand loyalty. For instance, in 2024, F5 reported strong customer retention rates, with a significant portion of its revenue coming from existing enterprise clients who rely on their security and application delivery services.
The intricate technology behind application delivery and security, featuring specialized algorithms for load balancing, traffic management, and sophisticated threat detection, presents a significant hurdle for potential new entrants. F5's extensive intellectual property, encompassing numerous patents and proprietary technologies, further complicates replication, requiring substantial investment and time for competitors to match its established capabilities.
Regulatory Compliance and Certifications
The cybersecurity and networking sectors demand rigorous adherence to industry standards and regulations like GDPR and HIPAA, alongside the acquisition of critical certifications. New companies entering this arena must commit substantial resources and time to navigate these complex compliance landscapes, presenting a significant barrier. F5's product portfolio is specifically engineered to assist its clientele in achieving and maintaining these essential regulatory obligations.
For instance, the increasing global focus on data privacy, exemplified by the General Data Protection Regulation (GDPR) which came into full effect in 2018 and continues to shape data handling practices, necessitates robust security measures. Companies failing to comply can face substantial fines, with GDPR penalties reaching up to €20 million or 4% of global annual turnover. This regulatory burden, coupled with the need for certifications such as ISO 27001, which demonstrates a commitment to information security management, creates a high entry cost for new players. F5's solutions often incorporate features that simplify these compliance efforts for their users.
- High Capital Investment: New entrants face significant upfront costs for legal counsel, compliance audits, and obtaining necessary certifications.
- Time to Market Delays: The lengthy process of achieving regulatory approval and certifications can delay a new company's ability to offer its products and services.
- Ongoing Compliance Burden: Maintaining compliance requires continuous investment in updates, training, and monitoring, adding to operational expenses.
- F5's Compliance Solutions: F5's offerings are designed to help customers meet stringent regulatory requirements, reducing the compliance burden and enhancing security posture.
Access to Distribution Channels and Ecosystem Partnerships
F5 Networks' established global network of partners, encompassing system integrators, resellers, and major cloud providers, presents a significant barrier to new entrants. This intricate web of relationships, cultivated over years, facilitates broad market penetration and customer access. For instance, F5's collaborations with cloud giants like AWS and Microsoft Azure ensure their solutions are readily available within those ecosystems.
The considerable time and financial investment required to replicate F5's extensive distribution channels and forge comparable strategic ecosystem partnerships, such as those with Equinix for colocation services or MinIO for object storage, pose a substantial hurdle. New companies would find it exceptionally difficult to quickly build this level of market reach and secure the necessary support to compete effectively.
- Distribution Network: F5's global partner ecosystem, including over 1,000 channel partners as of fiscal year 2023, provides significant market access.
- Ecosystem Integration: Deep integrations with leading cloud platforms like AWS, Azure, and Google Cloud are critical for customer adoption.
- Partnership Costs: Establishing and maintaining these relationships involves substantial ongoing investment and resource allocation.
- Competitive Disadvantage: New entrants face a steep climb to achieve similar reach and ecosystem leverage, impacting their ability to scale and compete.
The threat of new entrants in the application delivery and security market is considerably low due to the immense capital required for research and development. F5's consistent investment in advanced solutions like ADCs and WAFs necessitates substantial financial backing, making it difficult for newcomers to match the technological sophistication and performance levels. For example, F5's commitment to innovation is reflected in its significant R&D expenditures, which are crucial for staying ahead in this rapidly evolving sector.
Porter's Five Forces Analysis Data Sources
Our Porter's Five Forces analysis leverages data from company annual reports, industry association statistics, and market research reports to provide a comprehensive view of competitive intensity and strategic positioning.